- Feb 2, 2008
- 2,219
- 221
- 101
wccftech said:AMD x86 Zen Architecture Will Implement Game Changing Encryption Features Such as SME, SEV and HW Based SHA – Not Present In SkyLake or KabyLake
The first two are called SME and SEV, which stand for Secure memory Encryption and Secure Encrypted Virtualization. The third one is hardware based SHA (Secure Hash Algorithm). They are powered by a security co-processor. No competing Intel architecture has any known features to rival these.
http://wccftech.com/amd-zen-encryption-sme-sev-hw-based-sha/
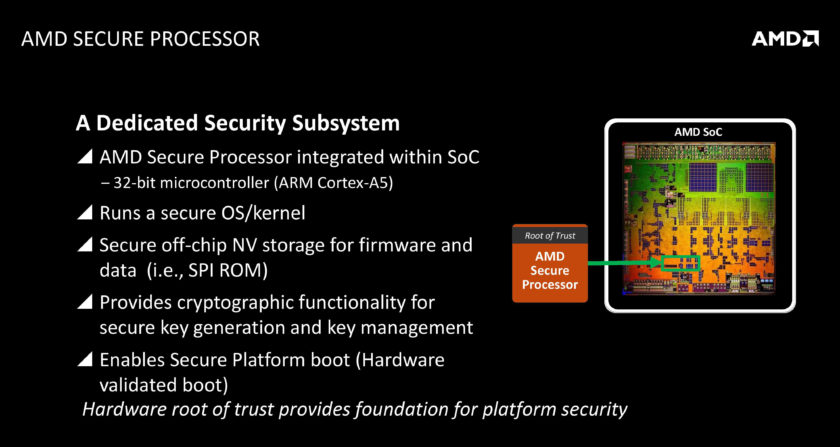
wccftech said:At the time of release, Zen will primarily compete against Skylake and Kaby Lake based processors, both of which lack the aforementioned features. It is not until Cannonlake and Coffee Lake that any semblance of parity is expected to be present between the two platforms – and even then it won’t be complete. All of this magic will happen, courtesy a “Security Co-Processor” that AMD has included inside of the Zen chip.
wccftech said:Zen SEV – the holy grail of secure cloud computing?
With the advent of NVDIMM (non volatile memory) however, this is going to become a very big problem, very fast. Unlike inherently volatile DIMMs, non volatile memory does not lose all data and this lowers the difficulty bar for a cyber attack by several orders of magnitude.
Intel has something called Software Guard Extensions, but this particular instruction set cannot be virtualized since the silicon giant does not have any complete memory encryption standard.
I guess AMD chose to put AVX-512 and such on the back burner in favor of this. A smart move?wccftech said:Zen will also contain hardware SHA – which means it’s going to offer significant performance improvement over previous iterations of AMD architectures and even Intel offerings! As far as we know, hardware based SHA will not be present in Intel offerings till Cannonlake arrives and we have already listed the major disadvantage of SGX – it cannot be virtualized.
So, we have government that gets upset when e-mail isn't private and controlled for it and enterprise (business and government) that gets upset when its data isn't private and controlled. As for the unwashed masses, we're told by Wired writers and others that we should never expect to have any privacy for our data. "All private citizen e-mail should be treated as public — with the expectation that anyone will be able to read it forever."wccftech said:Not even cloud providers (who have physical access to the servers) will be able to carry out any malicious actions against their clients, if they were so inclined. For all intents and purposes, the data of consumers would be well and truly safe.
Wouldn't it be interesting if these security features were to start benefiting enthusiasts and regular people. But, if you run Tails and TOR you're labeled an "extremist" by you know who — that same you know who that got upset over where "its" e-mails were stored. Getting official confirmation that Yahoo was doing everything possible to assist the spying on its users, the same company that suggested, years back, that it was doing everything possible to oppose this — gets a collective sigh of "Yeah, so?"
Maybe it's time for data and information security to be important for all of us, not just "enterprise". The double standard for data and privacy in general doesn't impress me.
Last edited:


