Stuka87
Diamond Member
- Dec 10, 2010
- 6,240
- 2,559
- 136
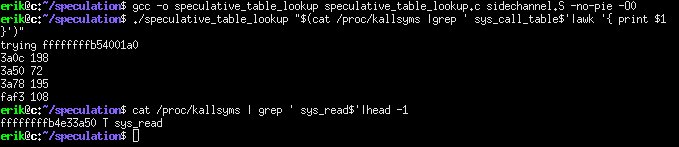
It all seems to be about accessing page tables which happen through the mmu and the translation look aside buffer and page tables in main memory.
This is about that.
https://lwn.net/Articles/569635/
Do you have detailed information about this Intel bug ?
It seems i have missed something when reading your post.
The one mentioned in the OP is on NDA until tomorrow, so we don't have exact details. The issue seems to be with Intel CPUs speculatively processing code before doing a permissions check which allows user level code to potentially have access to kernel level code.
The issue mentioned in the video is an attack on the MMU which can give access to memory addresses. This can allow an attacker to circumvent ASLR and read in memory contiguously that otherwise would have been randomized.