- May 4, 2000
- 16,068
- 7,380
- 146
https://www.tomshardware.com/news/eight-rtx-4090s-can-break-passwords-in-under-an-hour
Surely no hackers would dare buy eight whole RTX 4090 GPUs to do such a nefarious thing as break/collect/sell passwords though, so no worries there.
Security researcher Sam Croley took to Twitter to share just how incredible Nvidia's new RTX 4090 really is... at cracking passwords. It turns out it's twice as fast as the previous leader, the RTX 3090, at breaking one of your passwords — even when faced off against Microsoft's New Technology LAN Manager (NTLM) authentication protocol and the Bcrypt password-hacking function.
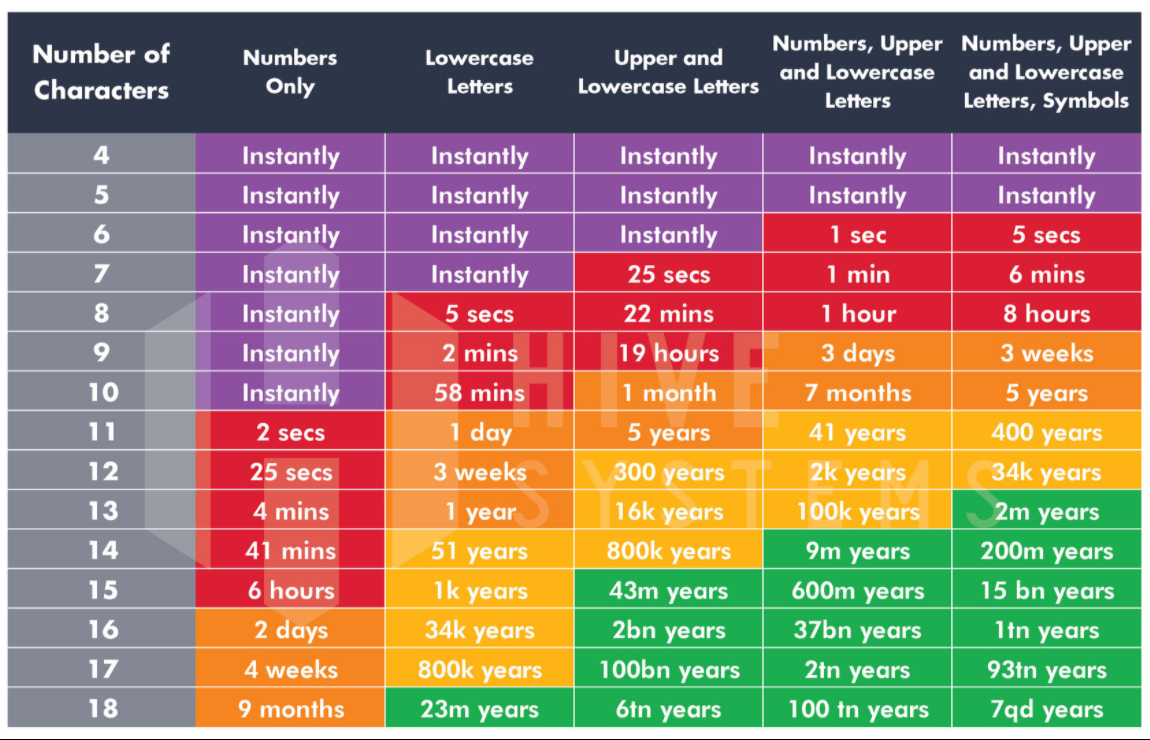
The researchers estimate that a purpose-built password hashing rig (pairing eight RTX 4090 GPUs) could crack an eight-character password in 48 minutes.
Of course, that assumes that the password is as least eight characters long and that it follows the required conventions (at least one number and a special character included). When HashCat is driven to test the most commonly used passwords, however, it can bring a theoretical 48 minute cracking operation that attempted all 200 billion possible combinations down to the millisecond range.
Surely no hackers would dare buy eight whole RTX 4090 GPUs to do such a nefarious thing as break/collect/sell passwords though, so no worries there.