It might not make it better, but it's a lot more accurate than saying NSA ransomware. An analogy would be a US weapons system in Afghanistan that get stolen by the Taliban and used it combat. Claiming "Afghan army hit by US missile strike" would be no less accurate than calling this NSA ransomware.Right, sorry okay. That makes it MUCH better. /s
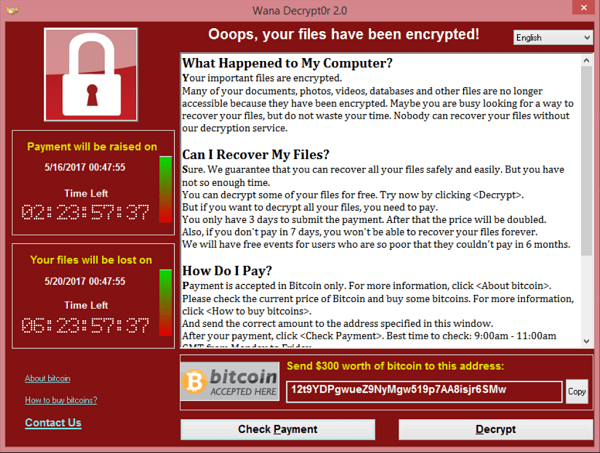
Any victims of Wanacry here?
Page 2 - Seeking answers? Join the AnandTech community: where nearly half-a-million members share solutions and discuss the latest tech.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
For mobile devices, sure. But for desktops/workstations? I wouldn't let people do that in a SMALL office in most cases, and I wouldn't even consider it in a large corporation. It's just not possible to guarantee that somebody's PC from home won't spread malware or otherwise interfere with the company network unless someone brings the hardware, company IT wipes the drive and reinstalls the OS and all security and management software, and then actively manages it at all times. But that's a headache as well trying to manage potentially thousands of different hardware configurations.
https://arstechnica.com/information...rything-or-the-rise-of-byod-in-the-workplace/
This has been gaining steam for about a decade. Instead of managing procurement of hardware. Resources are spent on erecting security policies. VDI can also play a role here.
Gryz
Golden Member
- Aug 28, 2010
- 1,551
- 204
- 106
We're not talking about BYODs.individual users are not allowed to bring their personal computing equipment
When you do software and hardware development, you need to lots of different equipment in your labs. Hardware and software for all kinds of purposes. Interoperability testing, packets sniffer or packet generating software running on windows, etc. All that stuff can not be managed by corporate IT, because then we would not get any work done.
All executives, managers, secretaries, product-managers, sales-people, HR, and whatever use laptops managed by corporate IT. But some people actually have to make the products that make money. You can not always force them into the mold of corporate IT.
Fardringle
Diamond Member
- Oct 23, 2000
- 9,200
- 765
- 126
BYOD is only growing in popularity.
We're not talking about BYODs.
Are you sure about that second comment?
dave_the_nerd
Lifer
- Feb 25, 2011
- 16,999
- 1,628
- 126
bigboxes
Lifer
- Apr 6, 2002
- 45,138
- 12,454
- 146
It might not make it better, but it's a lot more accurate than saying NSA ransomware. An analogy would be a US weapons system in Afghanistan that get stolen by the Taliban and used it combat. Claiming "Afghan army hit by US missile strike" would be no less accurate than calling this NSA ransomware.
Right. NSA created the exploit. Someone else added the payload.
dave_the_nerd
Lifer
- Feb 25, 2011
- 16,999
- 1,628
- 126
Right. NSA created the exploit. Someone else added the payload.
Since I thrive on being technically correct, would it be more correct to say that the NSA found the exploit. (Microsoft created it.) ?
I'll back you up on this.Since I thrive on being technically correct, would it be more correct to say that the NSA found the exploit. (Microsoft created it.) ?
thecoolnessrune
Diamond Member
- Jun 8, 2005
- 9,673
- 583
- 126
No, Microsoft had a vulnerability. The NSA created the exploit. Wannacry is the ransomware created from the exploit of the vulnerability.Since I thrive on being technically correct, would it be more correct to say that the NSA found the exploit. (Microsoft created it.) ?
Sent from my Nexus 7 using Tapatalk
bigboxes
Lifer
- Apr 6, 2002
- 45,138
- 12,454
- 146
No, Microsoft had a vulnerability. The NSA created the exploit. Wannacry is the ransomware created from the exploit of the vulnerability.
Sent from my Nexus 7 using Tapatalk
This.
dave_the_nerd
Lifer
- Feb 25, 2011
- 16,999
- 1,628
- 126
Red Squirrel
No Lifer
thecoolnessrune
Diamond Member
- Jun 8, 2005
- 9,673
- 583
- 126
Not at all. A vulnerability is a flaw in the system. Think of it as like a key lock that gets stuck pins. An exploit is something designed to take advantage of the vulnerability. This is like the lock pick set. The ransomware is software designed to use the exploit created for the vulnerability to hold objects for ransom. Think of it as a kidnapper taking your kid for ransom leveraging an exploit (lock pick set) created for a vulnerability (a lock that sticks pins).What's the difference between an exploit and vulnerability? Arn't they basically the same?
Sent from my Nexus 7 using Tapatalk
Red Squirrel
No Lifer
TIL. I always thought an exploit was just the presence of code that is vulnerable. If the exploit is the tool to use it, then wouldn't that make that the same as malware? The malware basically takes advantage of the vulnerability so it would be like the lock pick.
mnewsham
Lifer
- Oct 2, 2010
- 14,539
- 428
- 136
Yes, some malware can have multiple exploits using a half dozen vulnerabilities depending on what it's designed to do. This one was fairly simple ransomware, but that's hardly as bad as it could have been.TIL. I always thought an exploit was just the presence of code that is vulnerable. If the exploit is the tool to use it, then wouldn't that make that the same as malware? The malware basically takes advantage of the vulnerability so it would be like the lock pick.
Just look at Stuxnet. It employed four Zero-day vulnerabilities in a single worm in order to do it's task.
thecoolnessrune
Diamond Member
- Jun 8, 2005
- 9,673
- 583
- 126
You already stated the difference. An exploit is specifically the object (physical or software) used on the vulnerability. What you *do* with that with additional software or hardware determines whether it's malware, or desired software. Like how people would use an RGH hack on the Xbox 360 to install unlocked firmware. The exploit is the RGH hack. The payload you apply while it's in this vulnerable state is the malware, ransomware, or in this case, the software you want to be able to play games without piracy checks.TIL. I always thought an exploit was just the presence of code that is vulnerable. If the exploit is the tool to use it, then wouldn't that make that the same as malware? The malware basically takes advantage of the vulnerability so it would be like the lock pick.
Sent from my Nexus 7 using Tapatalk
Red Squirrel
No Lifer
So long story short, NSA did write wannacry then? But they just arn't the ones that released it in the wild? Or was wannacry just a variant of the NSA one? Either way, they wrote code to take advantage of a vulnerability right?
Elixer
Lifer
- May 7, 2002
- 10,371
- 762
- 126
No, NSA just had a exploit, they didn't create wannacry.So long story short, NSA did write wannacry then? But they just arn't the ones that released it in the wild? Or was wannacry just a variant of the NSA one? Either way, they wrote code to take advantage of a vulnerability right?
Wannacry used said exploit to encrypt all files and demand $$$ via bitcoin.
We don't know what NSA was using the exploit for, but you can bet they have no intention of letting people know anything about them being in their machines.
thecoolnessrune
Diamond Member
- Jun 8, 2005
- 9,673
- 583
- 126
NSA wrote the exploit. The thing that takes advantage of the flaw in Windows and SMB v1. Wannacry took NSA's exploit, and wrote software that, once the exploit was leveraged on the vulnerability, allowed an additional payload to be installed that encrypts the drive and holds the data for ransom.So long story short, NSA did write wannacry then? But they just arn't the ones that released it in the wild? Or was wannacry just a variant of the NSA one? Either way, they wrote code to take advantage of a vulnerability right?
Vulnerability
Exploit of the vulnerability
Ransomware using the exploit to access the system.
They all are different parts and different responsibilities. Wannacry's authors are the ones responsible for Wannacry's release. Exploits are created all the time to prove vulnerabilities exist. The NSA is guilty for gross negligence to the tech ecosystem for discovering a vulnerability, developing an exploit, and not reporting it to Microsoft. For anyone who appreciates an open tech community, this should immediately place the NSA on your crap list.
Sent from my Nexus 7 using Tapatalk
Elixer
Lifer
- May 7, 2002
- 10,371
- 762
- 126
Eh? Their #1 job is to gather intel, not to report exploits were found.The NSA is guilty for gross negligence to the tech ecosystem for discovering a vulnerability, developing an exploit, and not reporting it to Microsoft. For anyone who appreciates an open tech community, this should immediately place the NSA on your crap list.
Once they discovered their exploit(s) were out, they DID contact MS (and...) and tell them to patch ASAP.
What exactly is a "open tech community"?
There are tons of countries out there that have their internal version of spy agencies also actively try to make exploits, this isn't nothing new.
The linux kernel is open source, yet, there are a ton of exploits being written for it every day as well. Look at Android OS, there have been so many vulnerabilities in that, that it isn't funny, and what is worse is, they will NEVER patch those in some devices.
thecoolnessrune
Diamond Member
- Jun 8, 2005
- 9,673
- 583
- 126
What do you mean eh? It's an *extremely* simple concept. If you have any assumption that the NSA is the only that was likely to know of the exploit, that would be very misguided. The fact is that the exploit was known for some time, and had the possibility of being used by many groups, not just the NSA. That being done is negligence to the tech community. Wannacry's author's job was to write wannacry. It doesn't remove the issues it causes.Eh? Their #1 job is to gather intel, not to report exploits were found.
Once they discovered their exploit(s) were out, they DID contact MS (and...) and tell them to patch ASAP.
What exactly is a "open tech community"?
There are tons of countries out there that have their internal version of spy agencies also actively try to make exploits, this isn't nothing new.
The linux kernel is open source, yet, there are a ton of exploits being written for it every day as well. Look at Android OS, there have been so many vulnerabilities in that, that it isn't funny, and what is worse is, they will NEVER patch those in some devices.
What the NSA's job is 100% immaterial to removal of culpability.
Sent from my Nexus 7 using Tapatalk
Calling it negligence generally presupposes that the NSA owes a duty of care to the tech ecosystem.What do you mean eh? It's an *extremely* simple concept. If you have any assumption that the NSA is the only that was likely to know of the exploit, that would be very misguided. The fact is that the exploit was known for some time, and had the possibility of being used by many groups, not just the NSA. That being done is negligence to the tech community. Wannacry's author's job was to write wannacry. It doesn't remove the issues it causes.
What the NSA's job is 100% immaterial to removal of culpability.
Sent from my Nexus 7 using Tapatalk
Red Squirrel
No Lifer
NSA is more or less part of the bad guys - just a different group of bad guys than ones that write malware, so I would not be surprised that they don't want to report vulnerabilities, they rather take advantage of them.
TRENDING THREADS
-
Discussion Zen 5 Speculation (EPYC Turin and Strix Point/Granite Ridge - Ryzen 9000)
- Started by DisEnchantment
- Replies: 25K
-
Discussion Intel Meteor, Arrow, Lunar & Panther Lakes + WCL Discussion Threads
- Started by Tigerick
- Replies: 24K
-
Discussion Intel current and future Lakes & Rapids thread
- Started by TheF34RChannel
- Replies: 23K
-
-

AnandTech is part of Future plc, an international media group and leading digital publisher. Visit our corporate site.
© Future Publishing Limited Quay House, The Ambury, Bath BA1 1UA. All rights reserved. England and Wales company registration number 2008885.