I must say I am very impressed by what Microsoft is accomplishing with Windows Defender. Since the Fall 2017 update, they've managed to dramatically improve their detect rate (thanks to machine learning, A.I and cloud computing) to the point where, Windows Defender is actually quite comparable with top third party antimalware programs while still being free!
Now Microsoft is one upping the competition, because they've announced that Windows Defender can now be completely sandboxed.
Apparently this is a first for not only Microsoft, but for any other distributor of antimalware software. Windows Defender sandbox mode is not currently enabled in the latest official release of Windows 10. I believe it's enabled in the skip ahead version.
But you can force it (provided you're running Windows 10 version 1703 or later) if you want by using an elevated command prompt or windows powershell command, and RESTARTING (shutdown will not enable it due to a bug) your PC.
The command is:
So far though I haven't noticed any performance degradation or weirdness at all, so I'm keeping it enabled
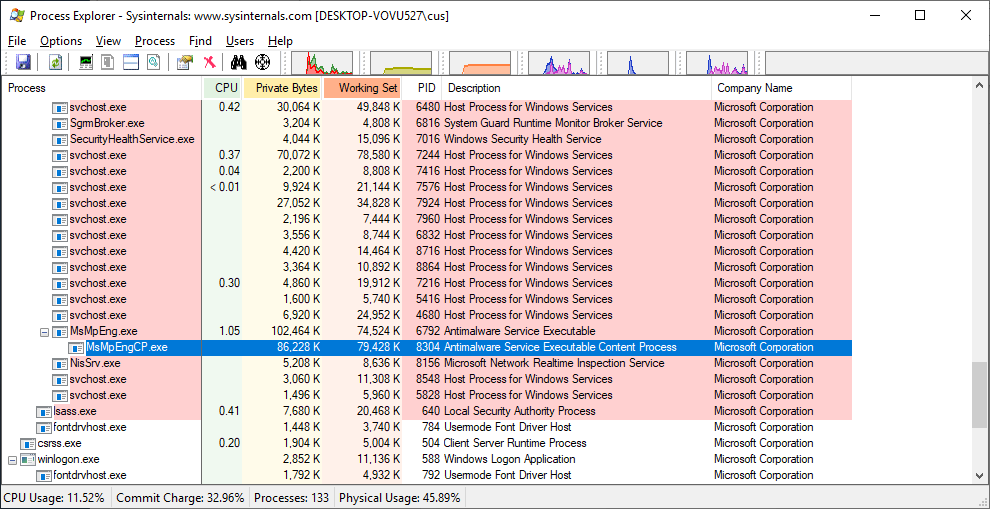
Once the sandboxing is enabled, customers will see a content process MsMpEngCP.exe running alongside with the antimalware service MsMpEng.exe.
Now Microsoft is one upping the competition, because they've announced that Windows Defender can now be completely sandboxed.
Apparently this is a first for not only Microsoft, but for any other distributor of antimalware software. Windows Defender sandbox mode is not currently enabled in the latest official release of Windows 10. I believe it's enabled in the skip ahead version.
But you can force it (provided you're running Windows 10 version 1703 or later) if you want by using an elevated command prompt or windows powershell command, and RESTARTING (shutdown will not enable it due to a bug) your PC.
The command is:
To turn it off, just put a 0 on the end and restart.setx /M MP_FORCE_USE_SANDBOX 1
So far though I haven't noticed any performance degradation or weirdness at all, so I'm keeping it enabled
Once the sandboxing is enabled, customers will see a content process MsMpEngCP.exe running alongside with the antimalware service MsMpEng.exe.



