Not sure if this should be posted under the motherboard section.
I was running the system PC health check if my pc would be able to run windows 11 , which it said no , does not specify why i assume because TPM 2.0 and secure boot requirements.
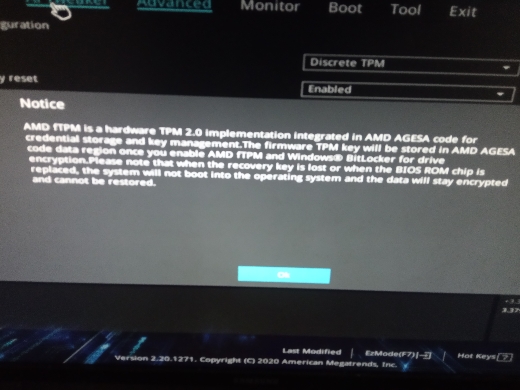
I do not have any TPM module on motherboard but i did enable fTPM under the AMD Bios option. This was not enough to make my PC ready for windows 11 , but it still booted.
So i disabled CSM , which make secure boot visible then under secure boot options i enabled it. But after rebooting no drives are visible to boot from expect a USB flash drive. is there anything i need to setup to have the drives appear?
There some options under secure boot BIOS menu but lo clue what to do and manual does not specify.
System spec :
Ryzen 1700
B350 Gaming 3 Gigabyte
16GB ram 2400
San disk ultra II , sata boot drive
Crucial Mx500 , sata
Kingston A2000, nmve
PS : also for anyone looking true manual , it is wrong many times where the default does not match the default in the bios.
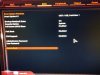
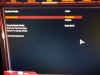
PSS : uploaded some bios pictures , first 2 pictures is secure boot on and the secure boot option page , 3th picture is with CSM on then it shows all drives.
I was running the system PC health check if my pc would be able to run windows 11 , which it said no , does not specify why i assume because TPM 2.0 and secure boot requirements.
I do not have any TPM module on motherboard but i did enable fTPM under the AMD Bios option. This was not enough to make my PC ready for windows 11 , but it still booted.
So i disabled CSM , which make secure boot visible then under secure boot options i enabled it. But after rebooting no drives are visible to boot from expect a USB flash drive. is there anything i need to setup to have the drives appear?
There some options under secure boot BIOS menu but lo clue what to do and manual does not specify.
System spec :
Ryzen 1700
B350 Gaming 3 Gigabyte
16GB ram 2400
San disk ultra II , sata boot drive
Crucial Mx500 , sata
Kingston A2000, nmve
PS : also for anyone looking true manual , it is wrong many times where the default does not match the default in the bios.
PSS : uploaded some bios pictures , first 2 pictures is secure boot on and the secure boot option page , 3th picture is with CSM on then it shows all drives.
Attachments
Last edited: