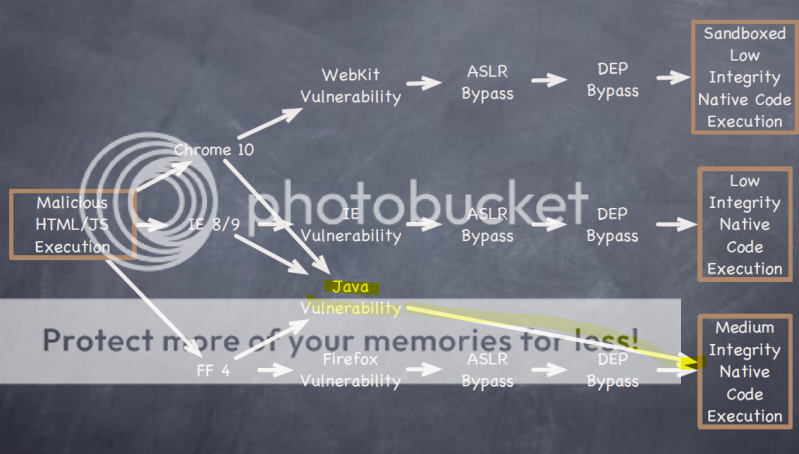
I got a bad virus yesterday named "Win 7 Security 2012". I tried several ways to delete from my system to no avail. I finally had to restore my computer to another earlier point, causing pain and suffering. But I got it running fine now.
Questions:
Shouldn't Win 7 have stopped it from installing? I thought this os was designed to prevent security problems like this.
Or maybe Microsoft Security Essentials should have stopped it?
Programs I have tried: Microsoft Security Scanner, Malicious Software Removal Tool, Security Essentials, Malwarebytes, Spyware Doctor and two others I don't remember.
Where did the virus come from? Was it probably an email?
What can I do to prevent this from happening again?
Questions:
Shouldn't Win 7 have stopped it from installing? I thought this os was designed to prevent security problems like this.
Or maybe Microsoft Security Essentials should have stopped it?
Programs I have tried: Microsoft Security Scanner, Malicious Software Removal Tool, Security Essentials, Malwarebytes, Spyware Doctor and two others I don't remember.
Where did the virus come from? Was it probably an email?
What can I do to prevent this from happening again?